Why CMMC Certification Matters
In today’s digital landscape, cybersecurity is a human endeavor rooted in protecting organizations, individuals, and sensitive data from emerging threats. Achieving CMMC (Cybersecurity Maturity Model Certification) demonstrates a commitment to safeguarding vital Department of Defense (DoD) data and is a crucial prerequisite for businesses working with the DoD. This certification enhances your organization’s cybersecurity posture and opens up new opportunities for securing government contracts. Our comprehensive process for achieving CMMC readiness offers a clear, step-by-step approach, automated document sorting, and takes care of the heavy lifting for you. This saves your company significant time, energy, and money.
The CMMC Assessment Process
The CMMC Assessment Process

Phase 1: Plan and Prepare the Assessment
The initial phase of the CMMC assessment process is all about thorough preparation, setting the stage for a smooth and successful audit. This phase begins with clearly defining the scope of the assessment and determining which systems, networks, data, and processes fall within the CMMC rigorous requirements. Proper scoping ensures that all critical components are addressed and minimizes surprises or gaps later in the process, laying a solid foundation for the assessment.
Equally important is preparing your personnel. Resource allocation and targeted training ensure that all relevant staff members understand their roles within the audit process. Employees should know what to expect, how their day-to-day responsibilities impact compliance, and how they contribute to a secure environment. This phase may include internal briefings, mock assessments, and focused training sessions to boost confidence and reduce uncertainty.
The overarching goal of the preparation phase is to eliminate ambiguity, enhance organizational readiness, and align practices with CMMC standards. Proactive measures at this stage pave the way for a streamlined, efficient assessment process, minimizing disruptions and maximizing the likelihood of achieving your desired level of certification.
Our product assists in reviewing, structuring, and aligning these materials with the specific requirements of the CMMC framework, ensuring readiness.
Phase 2: Conduct the Assessment
During this phase, a certified assessor conducts a comprehensive evaluation of your organization’s cybersecurity practices. The objective is to determine whether your security controls and processes meet your business’s specific CMMC maturity level. This phase includes a thorough review of technical measures, such as data protection strategies, access control mechanisms, incident response protocols, and more. It also extends to the operational aspects of your cybersecurity framework, like staff training effectiveness and day-to-day policy implementation.
The assessment process involves multiple evaluation methods, including technical testing, evidence collection, and interviews with key personnel. For instance, an assessor might test role-based access controls to confirm they are correctly enforced, examine activity logs to ensure compliance with security policies and verify user training records to confirm that staff understand and follow security protocols. This ensures that the controls are documented, effectively implemented, and maintained in practice.
A critical outcome of this phase is identifying gaps, deficiencies, or inconsistencies that could hinder your compliance efforts. The assessment is not merely about passing a checklist; it delves into the resilience and practicality of your organization’s cybersecurity framework. By understanding how well your security measures are integrated into everyday processes, you can address weaknesses, build more robust defenses, and mitigate risk. Failure to address these gaps could lead to potential security breaches, loss of sensitive data, and even loss of government contracts.
Meeting CMMC compliance standards is critical to protecting your business’s bottom line. Losing compliance can result in immediate disqualification from bidding on lucrative government contracts, the termination of existing agreements, and missed opportunities that competitors will seize. The financial impact, coupled with reputational damage, can put your business at a disadvantage in a highly competitive market. For companies that rely on government partnerships, compliance isn’t optional—it’s the key to sustaining and growing your business in this demanding sector.
The insights gained from this phase provide a clear picture of your compliance standing and actionable recommendations for improvement. The assessment lays the groundwork for achieving robust CMMC compliance by identifying areas of strength and opportunities for growth.
Phase 3: Report Assessment Results
Following the completion of the assessment, the certified assessor compiles a detailed report outlining the findings. This comprehensive report serves as a roadmap for your organization’s cybersecurity strategy, providing a transparent summary of strengths and areas requiring improvement. The report categorizes the findings according to compliance with specific CMMC practices, highlighting which requirements were met, where deficiencies exist, and how these may impact your overall certification goals.
The assessment results go beyond simply identifying compliance gaps; they offer context and an in-depth analysis of each issue. The assessor explains the nature of each deficiency, the associated risks, and the potential implications for your security posture and ability to meet DoD requirements. This contextual understanding helps your organization prioritize corrective actions and allocate resources effectively. The report also includes actionable recommendations, outlining specific steps to close identified gaps and strengthen overall security.
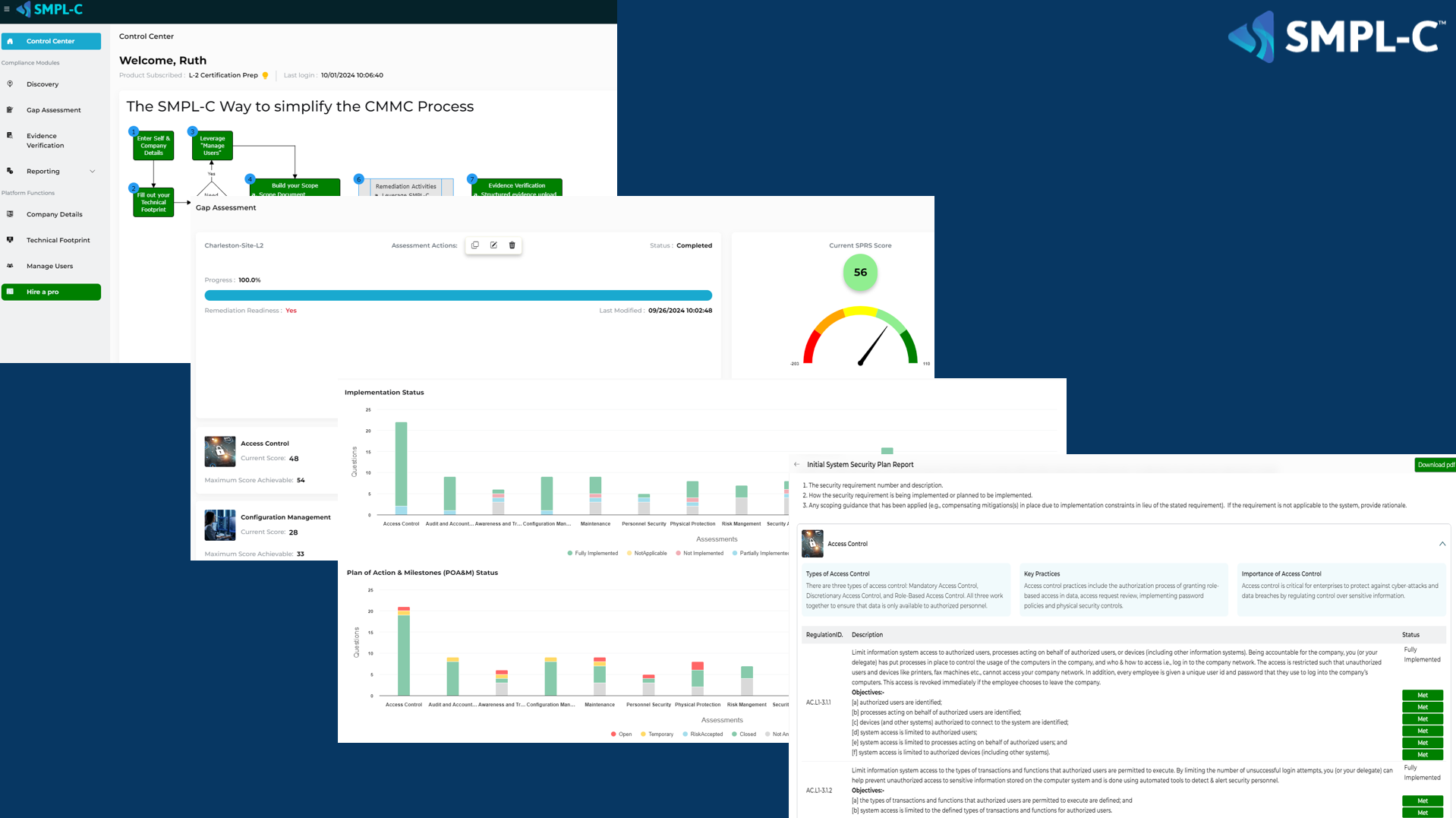
At SMPL-C, we simplify this process by providing an AI-powered platform that automates the bulk of the work. Instead of manually gathering and organizing evidence, we streamline the collection process, ensuring that all necessary documentation is available and up-to-date. Beyond just streamlining documentation, SMPL-C assists with identifying security gaps, creating remediation plans, and actionable insights to help you stay aligned with evolving CMMC standards. This saves you months of time and effort, allowing you to focus on your business operations rather than getting bogged down in compliance tasks.
In addition, our platform offers access to on-demand certified CMMC experts who can help guide you through any complexities and provide tailored advice when needed, without bloated retainer fees. Our software keeps you on the right track toward CMMC readiness, making compliance more manageable and less time-consuming.
The report provides a benchmark of your current compliance status but also serves as a roadmap for continuous improvement. By leveraging these findings, your organization can develop targeted action plans to address risks, strengthen security, and achieve CMMC certification. This approach ensures that your business not only meets DoD requirements but fosters a culture of ongoing resilience and cybersecurity vigilance, positioning you for long-term success.
Phase 4: Close-Out POA&Ms and Assessment
The final phase of the CMMC assessment process focuses on addressing any deficiencies identified during the assessment through a structured Plan of Action and Milestones (POA&Ms). This plan outlines each specific gap, the steps necessary to correct it, a timeline for completion, and the individuals or teams responsible for implementation. The objective is to achieve compliance and build a more robust, more resilient cybersecurity posture that can adapt to emerging threats.
Corrective actions during this phase may involve updating or creating new security policies, reconfiguring technical controls, deploying additional cybersecurity tools, conducting further staff training, or implementing new monitoring systems. The remediation process is collaborative, with the assessor working closely with your organization to ensure that all corrective actions are effective and meet the required CMMC standards.
Verification and validation are critical components of this phase. Once corrective actions have been completed, the assessor conducts follow-up reviews to confirm that all gaps have been fully addressed and that compliance has been achieved. Only after successful validation can the assessment be officially closed, marking the completion of your journey toward CMMC certification.
Achieving compliance through this structured approach positions your organization for DoD contracts and as a leader in cybersecurity excellence. CMMC certification is a direct gateway to securing government contracts, which are crucial for business growth. It also significantly impacts your reputation in the defense sector, demonstrating your commitment to robust cybersecurity practices. With CMMC becoming mandatory, achieving and maintaining compliance is essential for staying competitive in the marketplace. Certification opens new business opportunities, enhances your credibility, and fosters a culture of continuous improvement. By maintaining compliance through periodic reassessments and ongoing monitoring, your organization is better prepared to navigate future cybersecurity challenges, ensuring lasting security for your clients and stakeholders.
Key Benefits of CMMC Compliance

Key Benefits of CMMC Compliance


