
Zero-Trust Policy
Zero-trust policy is a security model that assumes that no user or device can be trusted by default. This means that access to resources is not granted based on location or network affiliation but on the user’s identity and behavior. Zero-trust policy is designed to protect organizations from data breaches and other security threats.
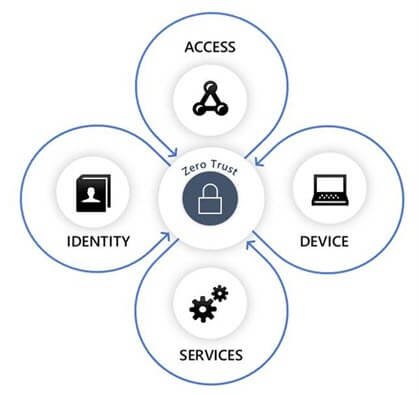
There are several key components of the zero-trust policy, including:
Micro-segmentation: This involves dividing the network into smaller zones, each with its own security controls. This makes it more difficult for attackers to move laterally within the network.
Least privilege: This means giving users and devices only the access they need to do their jobs. This helps to reduce the risk of unauthorized access to sensitive data.
Continuous monitoring: This involves constantly monitoring the network for signs of malicious activity. This helps to identify and respond to threats quickly.
Remediation: This involves taking steps to fix any security vulnerabilities that are found. This helps to prevent attackers from exploiting those vulnerabilities.
Zero-trust policy is a complex and evolving security model. However, it can be an effective way to protect organizations from data breaches and other security threats.
The NIST 800-171 framework is a set of cybersecurity requirements designed to help organizations protect their sensitive data from unauthorized access. In addition, the framework includes several controls that any organization can use to enforce a zero-trust policy.
Zero-trust policies assume that all users or devices cannot be trusted by default. Therefore, all access to resources must be verified and authenticated, regardless of whether the user or device is inside or outside the organization’s network. Organizations can use the NIST 800-171 framework to enforce a zero-trust policy by implementing the following controls:
Robust authentication: The framework requires organizations to implement strong authentication for all users and devices. This includes using multi-factor authentication (MFA) and passwordless authentication.
Least privilege: The framework requires organizations to implement least privilege access, meaning users should only be granted access to perform their job duties.
Micro-segmentation: The framework requires organizations to implement micro-segmentation. This security technique divides a network into small, isolated segments making it more difficult for attackers to move laterally within a network once they have gained access.
Continuous monitoring: The framework requires organizations to implement continuous monitoring. Organizations should continuously monitor their networks for signs of unauthorized activity.
By implementing these controls, organizations can enforce a zero-trust policy and protect their sensitive data from unauthorized access.
Benefits of Implementing a Zero-Trust Policy
There are several benefits to implementing a zero-trust policy. These benefits include:
Reduced risk of data breaches: A zero trust policy can help reduce the risk of data breaches by making it more difficult for attackers to access sensitive data.
Improved operational efficiency: A zero trust policy can improve operational efficiency by reducing the need for complex and time-consuming security policies.
Increased compliance: A zero trust policy can help organizations to comply with industry regulations, such as the Cybersecurity and Infrastructure Security Agency (CISA)’s Cybersecurity Framework (CSF).
Conclusion
The NIST 800-171 framework is a valuable tool for an organization to enforce a zero-trust policy. By implementing the controls outlined in the framework, organizations can reduce the risk of data breaches, improve operational efficiency, and increase compliance with industry regulations.


